Authentication
Configure authentication settings in EzeScan WebApps.
Provider
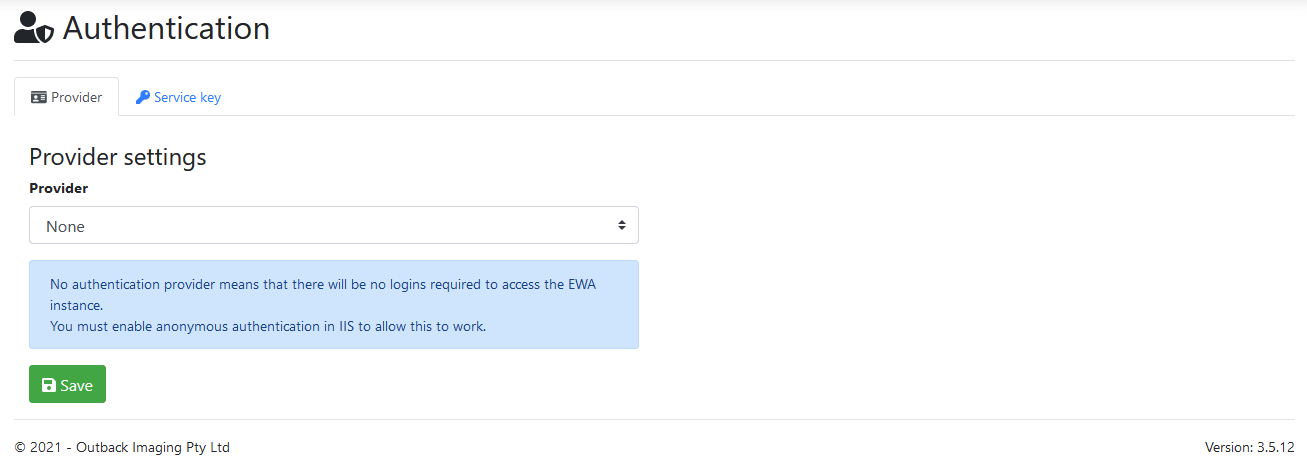
Provider:
Authentication provider to use for login requests.
Active Directory or Local Users
Local Users
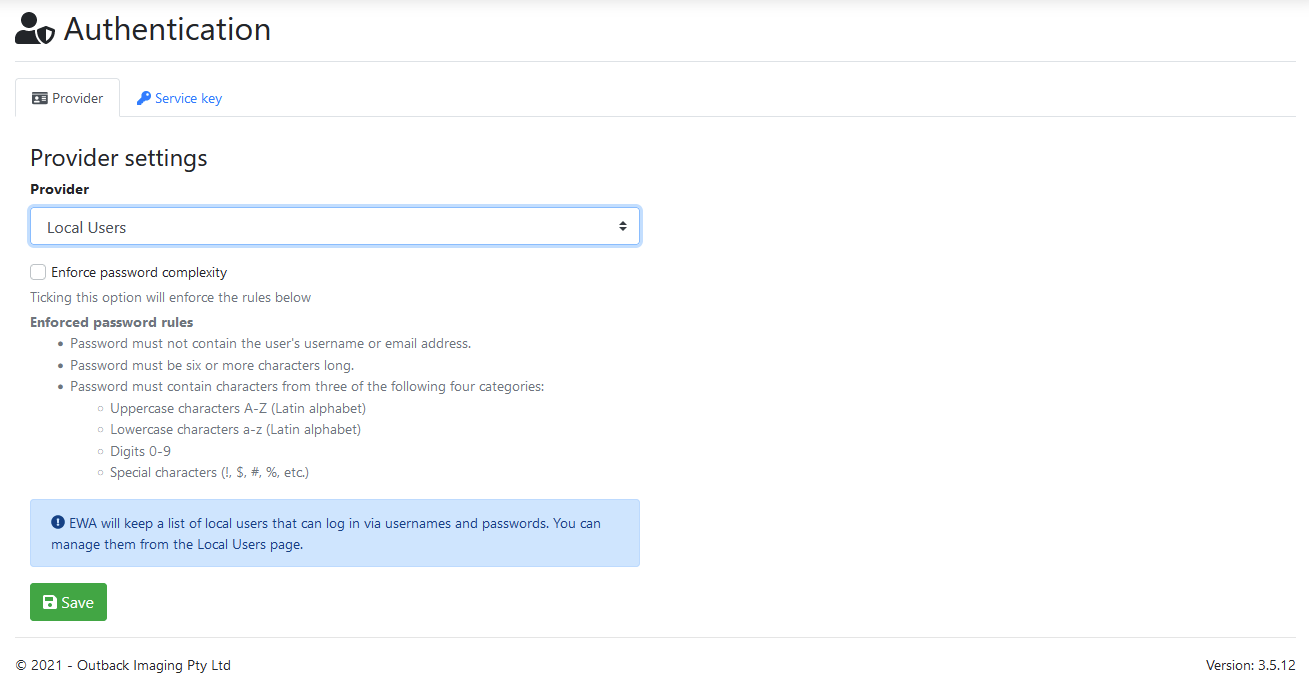
Enforce password complexity
Ticking this option will enforce the following rules:
Password must not contain the user's username or email address.
Password must be six or more characters long.
Password must contain characters from three of the following four categories:
Uppercase characters A-Z (Latin alphabet)
Lowercase characters a-z (Latin alphabet)
Digits 0-9
Special characters (!, $, #, %, etc.)
Active Directory
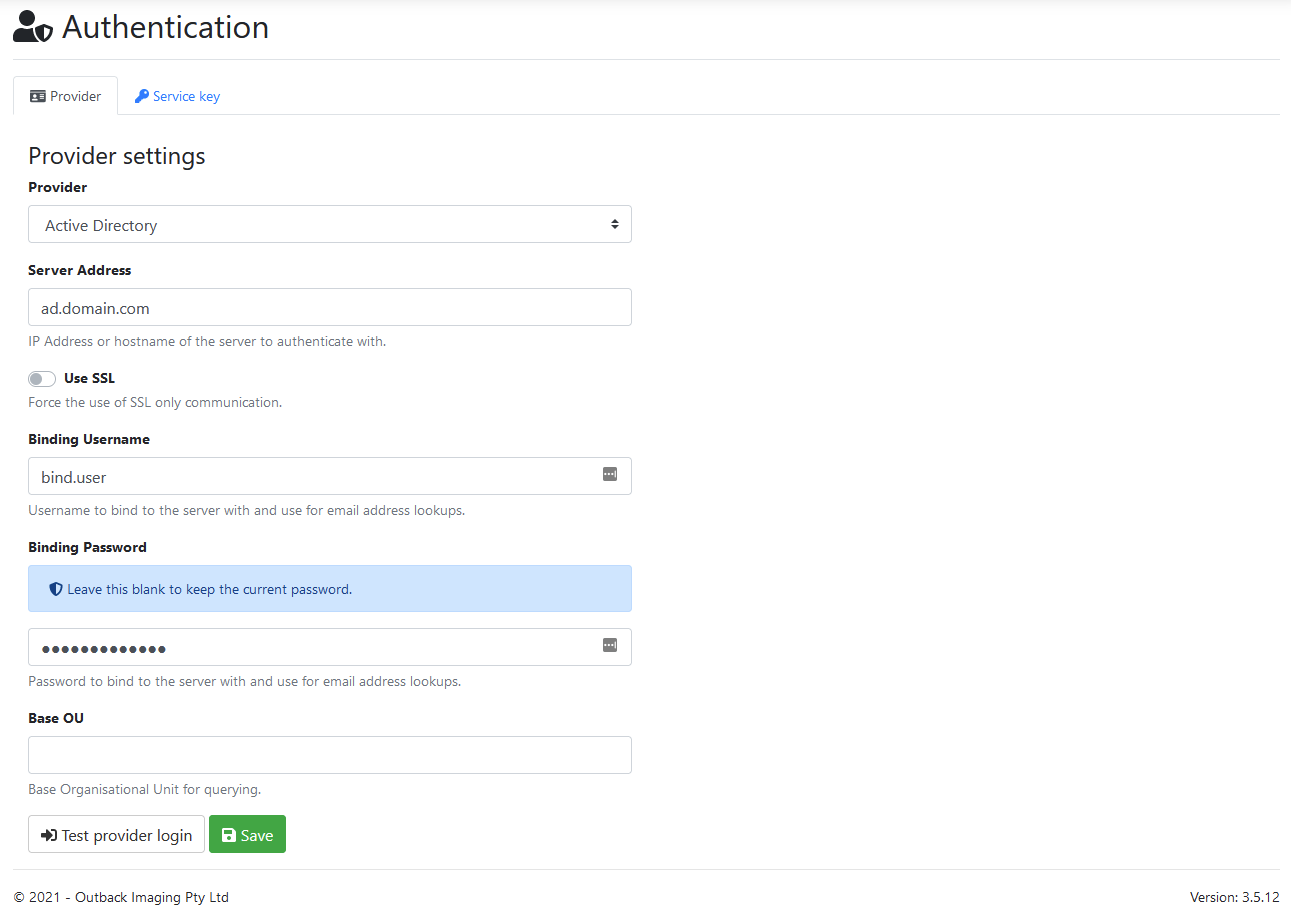
Server Address:
IP Address or FQDN of a domain controller.
(Usually just use the domain name as that resolves to one of the many available domain controllers within the domain, so if one goes offline we can try the next one).
Use SSL:
Force the use of SSL only communication.
Required if you want to force the use of LDAPS.
When using this option ensure you use the fully qualified domain name of the AD server in the ServerAddress field and specify port 636. (Out of the box AD domain controllers will only respond with LDAPS when using the machines host name, using an IP address will not work.)
eg dc01.ad.domain.com:636
By default the communication between EWA and active directly is already secure without enabling this option.
Binding Username:
The username of an active directory user that we can use to perform lookups of active directory users and groups.
(For testing purposes you can use any active directory user, even your own account!, for production use we recommend creating a service account in AD that we can use.)
Binding Password:
The password of an active directory user that we can use to perform lookups of active directory users and groups.
(For testing purposes you can use any active directory user, even your own account!, for production use we recommend creating a service account in AD that we can use.)
If the password field is not populated then the Test provider login button will test the connection using the saved password.
BaseOU:
This sets the root level of where our active directory queries should operate out of.
If left blank then all users and inside Active Directory will be able to log into EzeScan WebApps and all groups will be available when setting up permissions.
If set to a specific folder such as “OU=Users,OU=EzeScan,DC=domain,DC=ezescan,DC=com,DC=au” then only the AD users and groups within that folder will be able to login/be displayed when setting up permissions.
Service Key
Service keys allow applications to authenticate with our REST web services.
Examples of these applications are EzeScan Desktop/Server or EzeScan Capture for Ricoh.
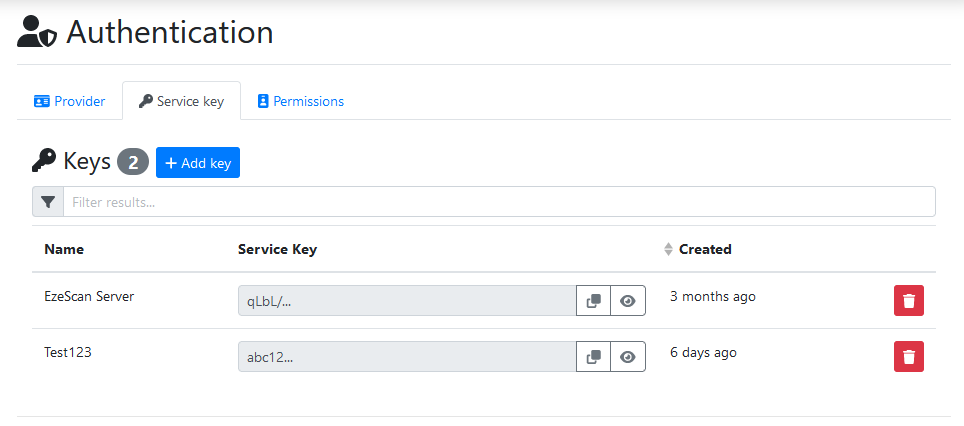
Click the Add Key button to create a new service key.
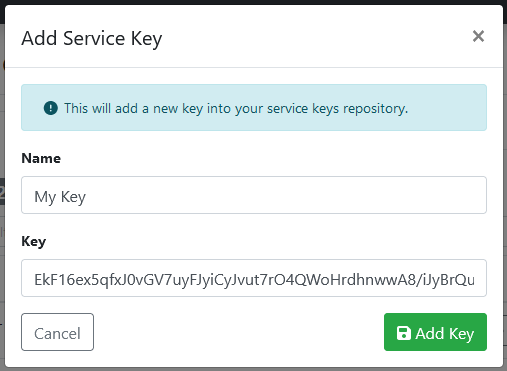
When adding a new key you are presented with the following settings:
Option | Description |
|---|---|
Name | The display name for the service key. |
Key | An auto generated key is provided, you are able to manually override the generated option. |
If you need to stop an application communicating with EzeScan WebApps then simply remove the service key it is using to authenticate.
We recommend creating separate service keys for each different application that is going to communicate.
Permissions
The permissions tab contains global settings relating to permissions within EzeScan WebApps.
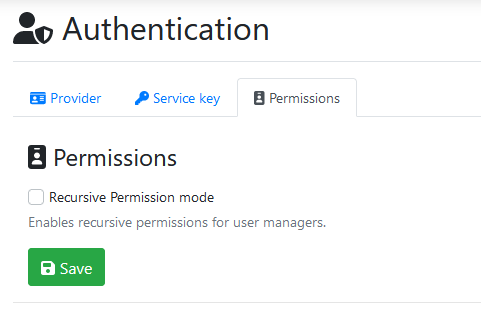
Recursive Permission mode
Enabling recursive permission mode will enable manager permission inheritance up to 11 levels deep.
By default managers only inherit permissions for users 1 level below them.
